|
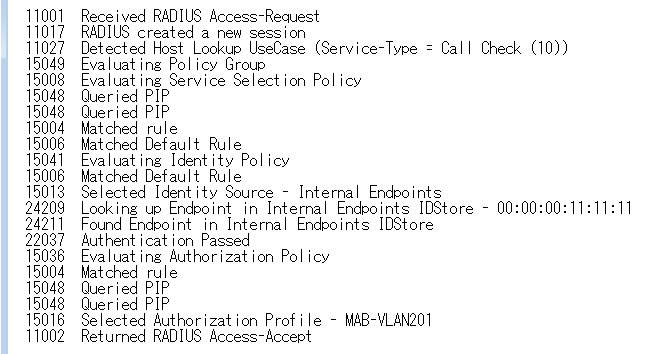
◆ Cisco ISE - MAB with Dynamic VLAN - Success !
・ Cisco ISE - Operations - Authentication - Details
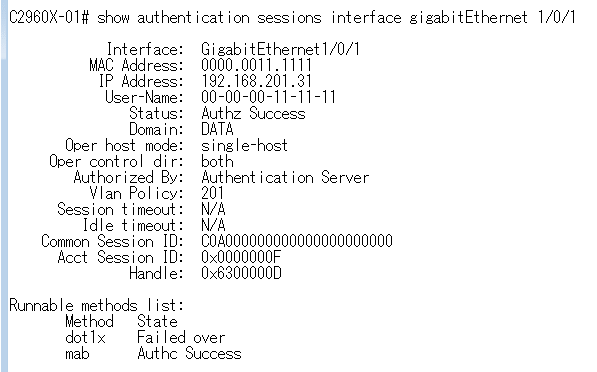
・ Catalyst 2960-X - IOS 15.x - show authentication sessions interface
gigabitEthernet 1/0/1
◇ Catalyst Switch - Success log
%AUTHMGR-5-START: Starting 'mab' for client (0000.0011.1111) on Interface
Gi1/0/1 AuditSessionID C0A000
%MAB-5-SUCCESS: Authentication successful for client (0000.0011.1111)
on Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-7-RESULT: Authentication result 'success' from 'mab' for client (0000.0011.1111) on
Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-5-VLANASSIGN: VLAN 201 assigned to Interface Gi1/0/1 AuditSessionID
C0A000
%EPM-6-POLICY_REQ: IP 0.0.0.0| MAC 0000.0011.1111| AuditSessionID C0A000| AUTHTYPE DOT1X| EVENT APPLY
%AUTHMGR-5-SUCCESS: Authorization succeeded for client (0000.0011.1111)
on Interface Gi1/0/1 AuditSessionID C0A000
◆ Cisco ISE - MAB with Dynamic VLAN + DACL - Success !
ISEで作成したAuthorization ProfileにDACLも指定している場合、15016 Selected Authorization
Profileと
11002 Returned RADIUS Access-Accept の間に以下のメッセージが出力されます。
⇒ 11022 Added the dACL specified in the Authorization Profile
また、Operations - Authentication - Details画面では別途DACL Download Succeededのログが残ります。
その中身は以下の3行だけです。
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
11002 Returned RADIUS Access-Accept
C2960X-01# show authentication sessions interface gigabitEthernet 1/0/1
Interface: GigabitEthernet1/0/1
MAC Address: 0000.0011.1111
IP Address: 192.168.0.1
User-Name: 00-00-00-11-11-11
Status: Authz Success
Domain: DATA
Oper host mode: single-host
Oper control dir: both
Authorized By: Authentication Server
Vlan Policy: 201
ACS ACL: xACSACLx-IP-PERMIT_ALL_TRAFFIC-537cb1d6
Session timeout: N/A
Idle timeout: N/A
Common Session ID: C0A000000000000000000000
Acct Session ID: 0x00000011
Handle: 0xCB00000F
Runnable methods list:
Method State
dot1x Failed over
mab Authc Success
%AUTHMGR-5-START: Starting 'dot1x' for client (0000.0011.1111) on Interface
Gi1/0/1 AuditSessionID C0A000
%LINK-3-UPDOWN: Interface GigabitEthernet1/0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/1,
changed state to up
%DOT1X-5-FAIL: Authentication failed for client (0000.0011.1111) on Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-7-RESULT: Authentication result 'no-response' from 'dot1x' for
client (0000.0011.1111) on Interface Gi1/0/1
AuditSessionID C0A000
%AUTHMGR-7-FAILOVER: Failing over from 'dot1x' for client (0000.0011.1111)
on Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-5-START: Starting 'mab' for client (0000.0011.1111) on Interface
Gi1/0/1 AuditSessionID C0A000
%MAB-5-SUCCESS: Authentication successful for client (0000.0011.1111) on Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-7-RESULT: Authentication result 'success' from 'mab' for client
(0000.0011.1111)
on Interface Gi1/0/1 AuditSessionID C0A000
%AUTHMGR-5-VLANASSIGN: VLAN 201 assigned to Interface Gi1/0/1 AuditSessionID C0A000
%EPM-6-POLICY_REQ: IP 0.0.0.0| MAC 0000.0011.1111| AuditSessionID C0A000|
AUTHTYPE DOT1X| EVENT APPLY
%EPM-6-AAA: POLICY xACSACLx-IP-PERMIT_ALL_TRAFFIC-537cb1d6| EVENT DOWNLOAD-REQUEST
%EPM-6-AAA: POLICY xACSACLx-IP-PERMIT_ALL_TRAFFIC-537cb1d6| EVENT DOWNLOAD-SUCCESS
%EPM-6-IPEVENT: IP 0.0.0.0| MAC 0000.0011.1111| AuditSessionID C0A000|
AUTHTYPE DOT1X| EVENT IP-WAIT
%AUTHMGR-5-SUCCESS: Authorization succeeded for client (0000.0011.1111)
on Interface Gi1/0/1 AuditSessionID C0A000
上記のようにsuccessログが出力していてもdACLの設定例が正しくない場合、CatalystにそのdACLの設定が
反映されません。よくある間違い例として、dACLで「送信元にanyを指定できていない」点が挙げられます。
Catalystに正しくdACLをダウンロードできた場合は、以下のようにdACLが加算されることを確認できます。
そもそもダウンロードできない場合にはISEで「Cisco AV PairのPriv15、Radius Service-type」のLoginを
attributeとして付加している事を再確認しましょう。
# show ip access-lists
Extended IP access list UNAUTH
10 permit udp any any eq bootps
20 permit udp any any eq domain
30 permit tcp any any eq domain
40 permit tcp any any eq www
50 permit tcp any any eq 443
60 permit ip any host 10.1.1.20
70 permit ip any host 10.1.1.20
Extended IP access list xACSACLx-IP-PERMIT_ALL_TRAFFIC-537cb1d6 (per-user)
10 permit ip any any
# show ip access-lists interface gigabitEthernet 1/0/1
permit ip host 192.168.0.1 any
|